Introduction
They say that dementia is being diagnosed in younger people. Trust me I can believe that statement, because I’ve spent the past couple of weeks banging my head against a brick wall just because people have been told by others to disable User Account Control (UAC) and modified their update settings.
The reality is that a few people who should know better, trust me they should know a lot better, has taken a telephone call from Microsoft engineers who have advised them that they have a serious security issue with their computer and need to run a program that will be sent to them via e-mail. But in order to run the program they need to disable User Account Control (UAC). Once they have given their e-mail address, they are told that the program has been sent to them. Whilst they are still talking to the Microsoft engineer, who has called them by the way, they mentioned that the e-mail had not arrived. They were advised to check their spam folder, and move the e-mail into their inbox and save the attachment before running the program.
Once they have run the program the caller says that the security issue has been resolved and after completing a quick telephone survey the caller has rung off, and they are left alone to happily use their compromised system.
One lady asked for help when she noticed that her computer would not connect to the internet, she thought “that the Microsoft engineer who called had possibly caused that issue, because she could surf the web before”
At least two of the computers I’ve worked upon, in the past couple of weeks, belong to system administrators, or senior IT managers who should know better.
Am I really surprised by this?
The easy answer is NO, because I know a very senior Infrastructural System Security Manager who once clicked upon a message that arrived through his corporate messenger system saying that the person – who he had never met or previously communicated with, had a picture of his Mother. Then wondered why his system became infected. Honestly I did not laugh loud enough; but I was also stunned both at the logic behind his stupidity and blind logic, that the message arrived through his corporate messenger and he knew that his computer system was so secure it could not be hacked.
I am stunned though by the number of people, who many would consider to be very educated and should know better, who will blindly accept the explanation that a Microsoft engineer will call them personally in order to resolve a very severe security issue.
I have to admit that the person who said they had lost money out of their bank account did report the situation to the police, and suffered the embarrassment of having to admit that they were stupid. Needless to say that I swapped out the hard drive and rebuilt the system. Whilst somewhat nasty, that person will – hopefully – never repeat that mistake again.
The result is that I’ve spent a while working on several other systems. A brief check-up found that the anti-virus software had been disabled, and a check-up concerning downloaded updates showed that the systems had not  been updated since patch-Tuesday in August.
been updated since patch-Tuesday in August.
If you happen to receive a telephone call from a Microsoft Professional who is offering to resolve a very serious security issue, please do what my other half does & tell them that you are running a Raspberry Pi, or PC-BSD.
PowerShell is a powerful tool
Clicking away at the command line gave a few answers, but PowerShell (PS) provided the answer to the problem.
I first used PS back in 2006, as it was introduced during the beta testing of Windows Vista. I hold my hands in the air and admit that I am the world’s worst scripter; & there are many who will testify to this statement. Whilst I am happy working with the command line, I felt uncomfortable using PS and shied away from using it.
What I failed to realise was that PowerShell offered a very powerful management interface to the user. It was only last year that I realised my mistake, and where I would stumble around PowerShell, using it as a convenient variant of the command line this time PowerShell provided the solution very quickly and I have started to appreciate that it was a powerful tool. Today I’m a lot more appreciative, and use it more often.
Windows Update using PowerShell
Okay, as I’ve already mentioned I am not a scripter so please forgive the long windedness of this post as I try and explain what I did. If you are still reading this I believe that you have a little knowledge concerning PowerShell – although that is not essential.
Rightio, it’s time to fill that flagon with a caffeine infused beverage …
Back in 2014 I was looking for another answer and stumbled across a post written by Michal Gaida who wrote a group of versatile scripts that have been bundled into the Windows Update Module for PowerShell that was posted upon the ‘Scripting Guys’ website (https://gallery.technet.microsoft.com/scriptcenter/2d191bcd-3308-4edd-9de2-88dff796b0bc).
Download PSWindowsUpdate.zip
Download the ‘PSWindowsUpdate.zip’, once the file has downloaded right-click the .zip file and select ‘Extract Here’
- %USERPROFILE%\Downloads\PSWindowsUpdate
Once the file has been extracted you need to launch PowerShell with ‘Administrator’ privileges. Once PowerShell has launched you need to modify the execution policy
- Set-ExecutionPolicy Unrestricted
Or
- Set-ExecutionPolicy RemoteSigned
Click ‘Yes’ or ‘Yes to All’
Now that you have extracted the file, you need to copy the folder to the modules folder. Yes there are a few ways that this can be achieved, either using Windows Explorer, the command line or because we already have PowerShell open we will use PowerShell.
Type the command
- Copy-Item –Path “C:\Users\yourprofile\Downloads\PSWindowsUpdate” –Destination “C:\Windows\System32\WindowsPowerShell\v1.0\Modules\PSWindowsUpdate” –Recurse –Force
This command is equivalent to either of the following commands entered at the command prompt (using Administrative privileges)
- XCopy %UserProfile%\Downloads\PSWindowsUpdate\*.* %WinDir%\System32\WindowsPowerShell\v1.0\Modules\*.* /h/i/c/k/e/r/y
Or
- RoboCopy %UserProfile%\Downloads\PSWindowsUpdate\ %WinDir%\System32\WindowsPowerShell\v1.0\Modules\ /CopyAll /E /R:0
Unblocking the extracted file
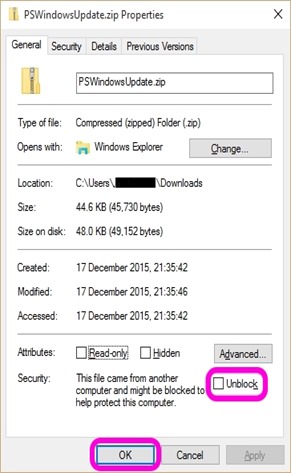 Now that you have copied the folder, and its contents, to the Modules folder you need to Unblock the folder. Although you have modified the execution policy you are still likely to receive ‘security warnings’ when you attempt to execute the commands. This is because PowerShell uses Internet Explorer’s zone settings, and the file that you have downloaded, extracted and copied, is marked as being delivered from the Internet Zone.
Now that you have copied the folder, and its contents, to the Modules folder you need to Unblock the folder. Although you have modified the execution policy you are still likely to receive ‘security warnings’ when you attempt to execute the commands. This is because PowerShell uses Internet Explorer’s zone settings, and the file that you have downloaded, extracted and copied, is marked as being delivered from the Internet Zone.
Again there are a couple of ways of ‘Unblocking’ the folder, and its contents,
The way to achieve this through PowerShell is
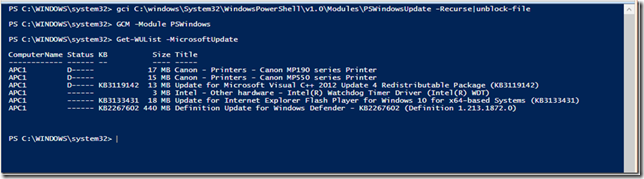
- Get-ChildItem C:\Windows\System32\WindowsPowerShell\v1.0\Modules\PSWindowsUpdate -recurse | unblock-file
Note
- The command Get-ChildItem can be abbreviated to ‘GCI’ or ‘gci’
- The ‘-Recurse’ switch unblocks parent and child folders. If this argument is omitted the child folders, and their contents, will be ignored and only those files held within the parent directory will be unblocked
If you are using the command line “Takeown /f:” C:\Windows\System32\WindowsPowerShell\v1.0\Modules\PSWindowsUpdate\*.*” /R
Note
/R is Recurse, and instructs the Takeown command to operate on files within the specified parent and child directories
You can also use Windows Explorer and navigate to the “C:\Windows\System32\WindowsPowerShell\v1.0\Modules” folder, right-click the “PSWindowsUpdate” folder selecting Properties, and then click ‘Unblock’ then OK.
Importing the module
Now that the files have been copied, and unblocked, you need to import the shared module in order to run the command. This is achieved by
- Import-Module C:\Windows\System32\WindowsPowerShell\v1.0\Modules\PSWindowsUpdate
The command Import-Module can be abbreviated using ‘ipmo’ instead of Import-Module.
Running Windows Update using PowerShell
Now that you have imported PSWindowsUpdate you need to know which commands are available to you. In order to achieve this you need to use the command
- Get-Command –Module PSWindows*
Or
- GCM –Module PSWindows*
Firstly you need to know what updates are available, this can be achieved by running
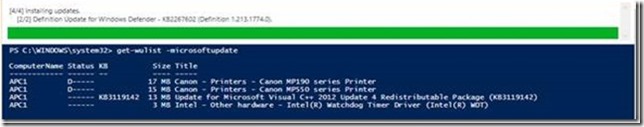
- Get-WUList –MicrosoftUpdate
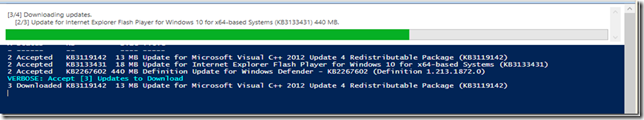
Then to download and install the available updates you need to run one of the following commands
- Get-WUInstall
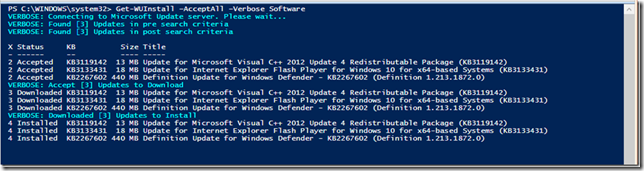
- Get-WUInstall –AcceptAll –Verbose Software
- Get-WUInstall –AcceptAll –Verbose Driver
- Get-WUInstall –AcceptAll –AutoReboot -Verbose